
It is no surprise to anyone that permitting new open pit mines in today’s environment is getting more difficult and even impossible in some areas. Underground mines also have their challenges, permitting as well as requiring relatively high grades to be economic.
So where might our future metal supplies come from? What are the options?
Insitu leaching may be the answer
 I recently came across an insitu leaching website, called BIOMore. This was an initiative sponsored by the EU that looked at insitu leaching technology for metal recovery. Environmental issues associated with mining in Europe, particularly open pit mining, raised concerns about how ore bodies in the EU might be developed in the future.
I recently came across an insitu leaching website, called BIOMore. This was an initiative sponsored by the EU that looked at insitu leaching technology for metal recovery. Environmental issues associated with mining in Europe, particularly open pit mining, raised concerns about how ore bodies in the EU might be developed in the future.
Insitu leaching technology was viewed as playing an important role. This is due to its minimal surface disturbance, ability to operate at great depth, and its potential in urban and developed locations. Sounds like a nice solution to have on hand.
The EU-funded BIOMOre research project was completed in 2018. It was designed to develop a new technological framework for the insitu recovering of metals from deep deposits. The process would rely on controlled stimulation of pre-existing fractures in combination with insitu bio-leaching. The study mainly focused on the application of existing technologies.
Fracing will be an issue
Insitu leaching essentially relies on exposing mineralized surfaces to leach solutions. This may require hydro-fracturing (fracing) to enhance insitu bio-leaching using bacteria and acid. Fracing is currently banned in some European countries so this is going to be a potential issue. From a leaching perspective, the trade-off would be between no fracing, reduced cost & lower metal recovery against higher cost & higher metal recovery with fracing.
If insitu leaching technology development is successful, it could help exploit European base metals from porphyry deposits (Cu, Au, Mo, Cu, REE, PGE, Re, Pb, Cu, Pt, Au) and other gold and uranium deposits. Insitu leaching would avoid building a mine, mine infrastructure, and it generates almost no tailings nor waste dumps. Leaching is expected to be cheaper than traditional mining and more acceptable to the public. Insitu leaching is being touted as “Green Mining”
What did they conclude
This study deliverables included comprehensive documentation, an economic evaluation, and risk analysis of a potential insitu bio-leaching operation. The basis was a theoretical deposit, looking at different well field set-ups.
 The study concluded that accessing potential deposits at depths of around 1000 m is economically feasible only if curved wells are used. The most relevant operational parameters are sufficient permeability in the ore zone and an adequate contact surface between the ore and leaching solution. The depth of the deposit is indirectly relevant, but more importantly the well installation cost per volume of deposit is critical. Hence curved wells are optimal.
The study concluded that accessing potential deposits at depths of around 1000 m is economically feasible only if curved wells are used. The most relevant operational parameters are sufficient permeability in the ore zone and an adequate contact surface between the ore and leaching solution. The depth of the deposit is indirectly relevant, but more importantly the well installation cost per volume of deposit is critical. Hence curved wells are optimal.
One interesting suggestion was combining an insitu leach operation with geothermal energy recovery. This might result in additional project revenue stream with only a marginal cost increase.
It was suggested that insitu leach operations might be attractive in former mining regions where high grade deposits have been mined out yet nearby low grade deposits are well defined. Social license for insitu leaching may also be more accepting in these areas.
If you are interested in learning more about insitu leaching technology and the chemistry aspect, the BIOMore study deliverables are available for downloading at this site.
In the past, mining engineers like myself were told to learn the basics of crushing, grinding, and flotation to become more well rounded. I may suggest that future mining engineers may need to learn the basics of directional drilling, hydro-fracing, and chemistry. Sounds like petroleum engineering.
Update: The University of Western Australia is also looking at electric fields to extract metals from hard rock ore, the sample principle as electro-plating. Check out more information at this link “No more digging – a new environmentally friendly way of mining“.
Some aspects are still uncertain


 I am also curious about the ability to finance such projects, given the caution associated with any novel technology. Many financiers prefer projects that rely on proven and conventional operating methods.
I am also curious about the ability to finance such projects, given the caution associated with any novel technology. Many financiers prefer projects that rely on proven and conventional operating methods.
 With regards to blockchain, it seems to me the main benefits are being related to supply chains, whether for purchasing or selling activities. Some of the examples given are that one can verify where the cobalt in your phone was mined or where your engagement diamond is from. Oddly though, I don’t recall ever wanting to know where the metal in my phone is from.
With regards to blockchain, it seems to me the main benefits are being related to supply chains, whether for purchasing or selling activities. Some of the examples given are that one can verify where the cobalt in your phone was mined or where your engagement diamond is from. Oddly though, I don’t recall ever wanting to know where the metal in my phone is from. We have seen in manufacturing that robotics will eliminate repetitive type jobs. Will robotic process automation (rPA) be able to do the same by completing repetitive tasks for us?
We have seen in manufacturing that robotics will eliminate repetitive type jobs. Will robotic process automation (rPA) be able to do the same by completing repetitive tasks for us? Collecting hoards of data from a site wide sensor network creates a dilemma in what to do with all the data collected. Smart cities are running into this issue. Who can sort through the data, decide what is important and what is noise, then summarize the data and report on it in real time? A human cannot deal with the amount of data being collected in such networks.
Collecting hoards of data from a site wide sensor network creates a dilemma in what to do with all the data collected. Smart cities are running into this issue. Who can sort through the data, decide what is important and what is noise, then summarize the data and report on it in real time? A human cannot deal with the amount of data being collected in such networks. Regarding the two technologies discussed in this blog, I personally feel robotic process automation will have far greater impact on mining industry future and its profitability.
Regarding the two technologies discussed in this blog, I personally feel robotic process automation will have far greater impact on mining industry future and its profitability.
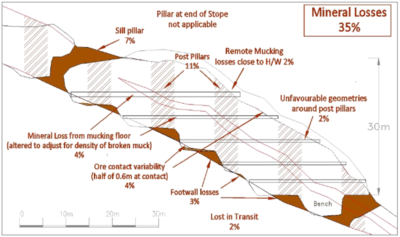 I am not going into detail on Paul’s paper, however some of my key takeaways are as follows. Download the paper to read the rationale behind these ideas.
I am not going into detail on Paul’s paper, however some of my key takeaways are as follows. Download the paper to read the rationale behind these ideas. The bottom line is that not everyone will necessarily agree with all the conclusions of Paul’s paper on underground dilution. However it does raise many issues for technical consideration on your project.
The bottom line is that not everyone will necessarily agree with all the conclusions of Paul’s paper on underground dilution. However it does raise many issues for technical consideration on your project.




 Its the right thing to do
Its the right thing to do The company gets a chance to learn about potential employees and also gets productive service from them.
The company gets a chance to learn about potential employees and also gets productive service from them.
 His topic is interesting and relevant to today’s mining industry. Paul raised many thoughtful points supported by data. He gave me permission to share his information.
His topic is interesting and relevant to today’s mining industry. Paul raised many thoughtful points supported by data. He gave me permission to share his information. I agree with many of the points raised by Paul in his study. The mining industry has some credibility issues based on recent performance and therefore understanding the causes and then repairing that credibility will be important for the future.
I agree with many of the points raised by Paul in his study. The mining industry has some credibility issues based on recent performance and therefore understanding the causes and then repairing that credibility will be important for the future.



 From time to time the Landslide Blog will examine mine slopes, tailings dams, and waste dump failures, however much of their information relates to natural earth or rock slopes along roads or in towns.
From time to time the Landslide Blog will examine mine slopes, tailings dams, and waste dump failures, however much of their information relates to natural earth or rock slopes along roads or in towns.

 Sensors are the answer
Sensors are the answer Their belt conveyor systems (
Their belt conveyor systems (
 Do the opposite
Do the opposite Different companies have different corporate objectives and each mining project will be unique with regards to the impacts of cutoff grade changes on the orebody.
Different companies have different corporate objectives and each mining project will be unique with regards to the impacts of cutoff grade changes on the orebody.